Services for cyber security guard against harmful assaults, unauthorized access, and inappropriate usage of computers, servers, mobile devices, electronic systems, networks, and data.
With cybersecurity breaches becoming more common, businesses must closely monitor their security measures. Whether implementing security measures before a hack occurs or hiring a cybersecurity service, here are the top features to look for in a cybersecurity system for a company.
Security
As data, systems, and networks become increasingly complex, preventing and responding to unauthorized access is critical. Unauthorized access costs time and money and can damage sensitive information and cause loss of trust and reputation.
Security services can help businesses protect against unauthorized access by detecting and analyzing software, hardware, and network vulnerabilities. They can then recommend and implement solutions to remedy those vulnerabilities.
For example, security services may analyze network traffic and detect if hackers have modified or deleted data. They could also apply forensic analysis to determine what went wrong and what can be done to fix it.
Cyber security services can also provide backups and recovery strategies for organizations to continue operating after a cyber incident. These backups and recovery strategies can ensure that critical files and systems remain accessible and that customers’ data is not lost during a cybersecurity attack.
Compliance
Compliance services help organizations remain up-to-date with governmental and industry standards. They also help businesses build credibility by adhering to these regulations, which can be helpful when acquiring investors and sanctioning loans.
Some compliance services protect against unauthorized access to data, systems, and networks by identifying, tracking, and responding to incidents. It can be essential in the wake of a data breach, where the resulting damage may go beyond time and money.
For instance, companies that handle sensitive personal information such as names, addresses, credit card numbers, and medical records must adhere to rules set forth by the Payment Card Industry Data Security Standard (PCI DSS). It includes developing policies and procedures that safeguard this data from unauthorized access and documenting these processes.
A good compliance service provider will guide you through all the steps involved in achieving and maintaining regulatory compliance, which can help ensure your business stays out of trouble with regulators. They will also help you navigate the often complex process of complying with industry standards, saving you time and money.
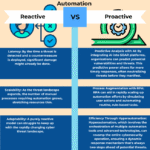
Automation
Automation is a technology that uses preprogrammed commands and feedback controls to perform an activity. Automated systems are typically more intelligent than human counterparts and can carry out specific tasks faster.
In addition to being less expensive than hiring a full-time employee, automation can also improve the quality of work by eliminating mistakes and time-consuming tasks. As a result, IT professionals may focus on higher-level jobs that demand more human expertise and abilities by automating repetitive and time-consuming processes.
Security teams can use automation to search through their networks for advanced threats. By proactively identifying unusual network traffic, login anomalies, suspicious database-read volumes, and system file changes, bots can automatically alert a human analyst to potential issues.
Security automation tools can help reduce the amount of data that security teams need to process, preventing the proliferation of false positives. In addition, it means that security teams can more quickly detect and respond to cybersecurity events.
Visibility
Visibility is seeing what’s going on within and moving through your network. That means knowing everything from network traffic and monitoring applications to managed network resources and big data analytics.
When it comes to cyber security, complete visibility can help you protect against unauthorized access by hackers. It also allows security analysts to identify vulnerabilities and take action before an attack occurs.
Another essential part of network visibility is monitoring the usage of transient devices, such as smartphones and tablets. They are a popular target for malware, and when not properly managed, they can give criminals a direct path into your systems.
Keeping track of these tiniest machines and ensuring they comply with policies takes time and effort. But the challenge worsens when they contact other network services, like cloud services.
Scalability
Scalability refers to a system’s ability to accommodate an increased workload without causing significant performance problems. In addition, this quality attribute can protect against unauthorized access to sensitive data, which is essential for businesses that want to maintain their competitive edge in the digital age.
A scalable system should handle increases in volume and traffic from item scanning, for example, while maintaining high responsiveness. In addition, it can use new capabilities like faster processing or more extensive data storage.
In software, scalability is a quality attribute that can be measured using various performance metrics. These metrics include response time, throughput, and resource usage.
When analyzing an application’s scalability potential, define the essential values to measure and use as a performance and scalability testing benchmark. It will allow you to identify and address performance bottlenecks in your system before they become a problem. It also helps you choose the most appropriate scalability model for your applications. You can also use scalability analysis to reduce the cost of scaling up or down your software.